
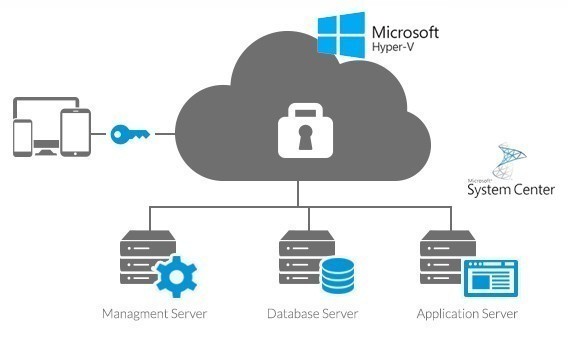
An on-premises infrastructure, or private cloud, and a public cloud are combined to form a hybrid cloud. Data and apps can travel between the two environments thanks to hybrid clouds.

Our offerings include:



WhatsApp us